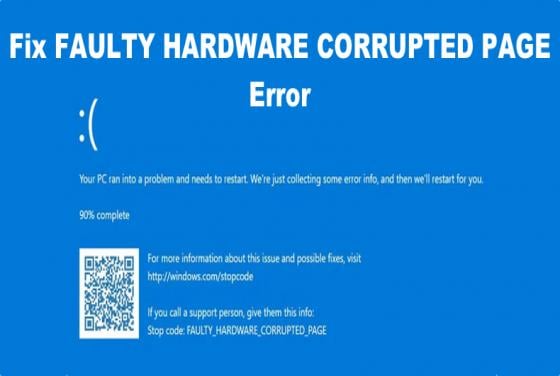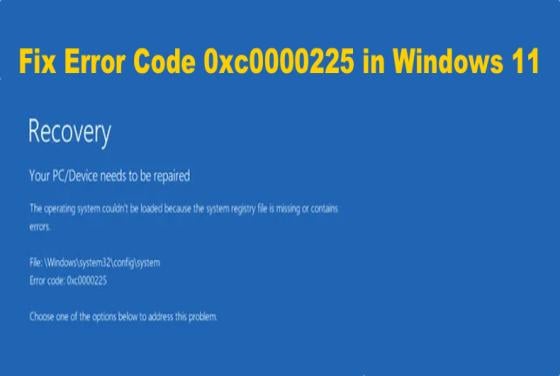

How to Fix Error Code 0xc0000225 in Windows 11
If you started getting Error Code 0xc0000225 when booting up your Windows 11 computer, it usually means that Windows can’t find vital system files used for booting. This article will describe the most important aspects of this problem and show you how to fix it. Error Code 0xc0000225 mea