AMBA Website Ransomware
What is AMBA?
AMBA is ransomware-type virus that targets Russian websites. After infiltrating the server, AMBA encrypts most files on the system and adds the .AMBA or .RROD extension to the name of each encrypted file. A text file ("ПРОЧТИ_МЕНЯ.txt") is then created that contains a message (in Russian) encouraging server owners to contact cyber criminals via the email address provided.
The message states that files have been encrypted and that users must contact developers of AMBA to receive decryption instructions. Victims are also warned not to try to restore files using third party tools, since this action would supposedly corrupt encrypted files. This behavior is common to ransomware-type viruses. Once contacted, victims receive a reply stating that they must pay a ransom to receive a decryption key. The size of ransom is currently unknown, however, many ransomware viruses demand between 0.5 and 1.5 Bitcoins (at time of research, 1 Bitcoin was equivalent to $673.21) Cyber criminals request payment in Bitcoins to enable them to remain anonymous. In fact, cyber criminals often ignore victims whether they pay or not. Therefore, you are strongly advised to ignore these requests and never attempt to pay or contact these people. At time of research, there were no tools capable of restoring files encrypted by AMBA. Therefore, you can only restore your data from a backup.
Screenshot of a message encouraging users to contact the developers of AMBA ransomware to decrypt their compromised data:
AMBA is very similar to KimcilWare and CTB-Locker and many other viruses. All encrypt files and make ransom demands. Most use an asymmetric encryption algorithm and, thus, the only noticeable difference between them is the size of ransom. Ransomware-type viruses are mostly distributed via infectious email attachments (for example, fake job application forms), P2P (peer-to-peer) networks (for example, Torrent), fake software updaters, and trojans. Therefore, be cautious when downloading files from third party sources and when opening attachments sent from unrecognized/suspicious email addresses. Furthermore, keep your installed software updated and use a legitimate anti-virus/anti-spyware suite. The key to computer safety is caution.
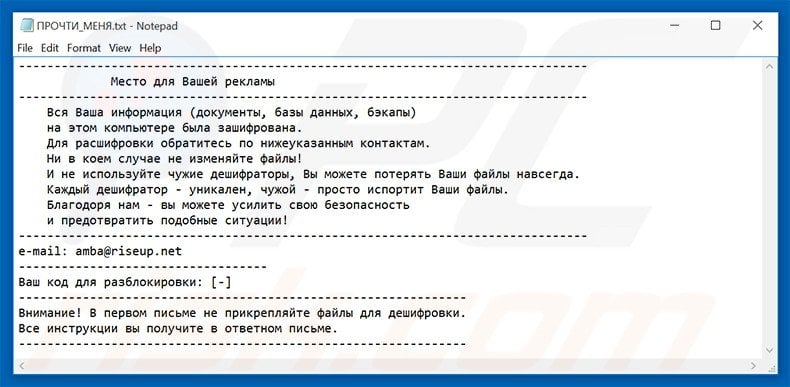
Text presented in "ПРОЧТИ_МЕНЯ.txt" file.
--------------------------------------------------------------------------------
Место для Вашей рекламы
--------------------------------------------------------------------------------
Вся Ваша информация (документы, базы данных, бэкапы)
на этом компьютере была зашифрована.
Для расшифровки обратитесь по нижеуказанным контактам.
Ни в коем случае не изменяйте файлы!
И не используйте чужие дешифраторы, Вы можете потерять Ваши файлы навсегда.
Каждый дешифратор - уникален, чужой - просто испортит Ваши файлы.
Благодоря нам - вы можете усилить свою безопасность
и предотвратить подобные ситуации!
--------------------------------------------------------------------------------
e-mail: amba(@)riseup.net
-----------------------------------
Ваш код для разблокировки: [-]
---------------------------------------------------------------
Внимание! В первом письме не прикрепляйте файлы для дешифровки.
Все инструкции вы получите в ответном письме.
---------------------------------------------------------------
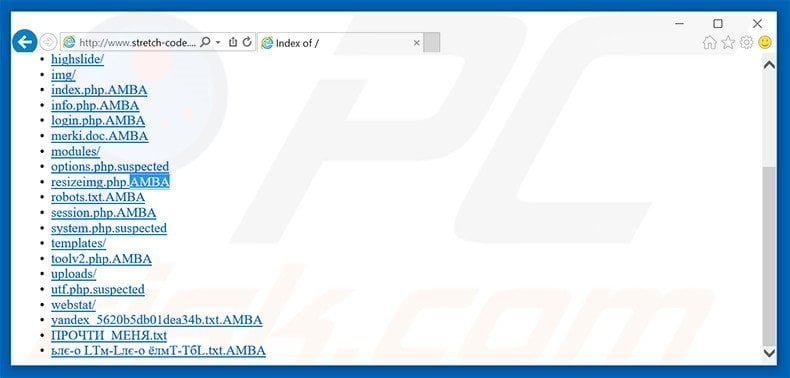
Screenshot of a server infected with AMBA ransomware:
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.

▼ Show Discussion