KimcilWare Website Ransomware
What is KimcilWare Ransomware?
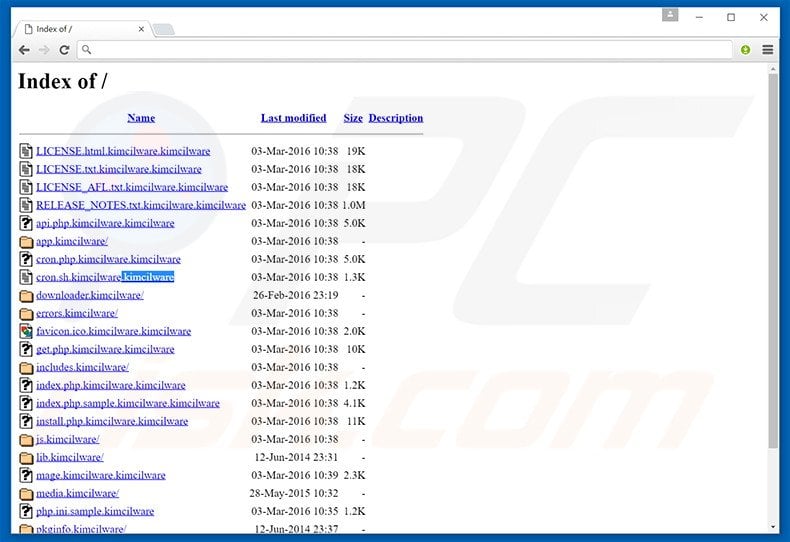
KimcilWare ransomware targets websites using the Magento e-commerce platform (currently, it is not confirmed whether KimcilWare infects other platforms). During encryption, this ransomware adds a .kimcilware to each file stored on the server. Furthermore, it creates an index.html file containing a ransom-demanding message.
The message states that files stored in the server have been decrypted. Victims are instructed to pay a $140 ransom in Bitcoins. Victims must contact cyber criminals via an email address provided ([email protected]). Research shows that there is another variant of KimcilWare using a different script to encrypt the files. This version adds a .locked file extension rather than the aforementioned .kimcilware.
Furthermore, the second variant does not change index.html. Instead, it creates a README_FOR_UNLOCK.txt file containing a message stating that the files have been encrypted. The ransom demanded by this variant is 1 Bitcoin (~$413.43). Unfortunately, there are no tools capable of restoring compromised data. Therefore, the only solution to this problem is to restore your files and data from a backup.
Screenshot of a message encouraging users to contact the developers of KimcilWare ransomware to decrypt their compromised data:
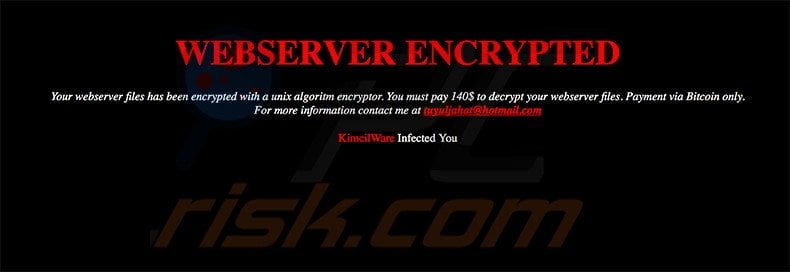
Research shows that ransomware-type viruses are often very similar. For instance, KimcilWare, Locky, CTB-Locker, Xorist, Vault, and Cerber also infiltrate systems and encrypt stored files.
Unlike KimcilWare, however, most ransomware infections (including those listed here) are designed to target the Windows OS. There are two other significant differences between these viruses - encryption type used and size of the ransom.
Paying the ransom does not guarantee that your files will be decrypted. In fact, cybercriminals often do not respond to victims even if payment is made.
For this reason, you should never attempt to pay the ransom or contact cybercriminals. Ransomware is mainly distributed via trojans, fake software updates, malicious email attachments, and peer-to-peer (P2P) networks.
Therefore, you should keep all installed software up-to-date and use a legitimate anti-virus/anti-spyware suite. In addition, be cautious when downloading files/applications from third-party sources and opening files sent from unrecognized and/or suspicious emails.
Message in README_FOR_UNLOCK.txt file:
ALL YOUR WEBSERVER FILES HAS BEEN LOCKED
You must send me 1 BTC to unlock all your files.
Pay to This BTC Address: 1859TUJQ4QkdCTexMTUQYu52YEJC49uLV4
Contact [email protected] after you send me a BTC. Just inform me your website url and your Bitcoin Address.
I will check my Bitcoin if you really send me a BTC I will give you the decryption package to unlock all your files.
Hope you enjoy ;)
Screenshot of an infected web server containing files with the .kimcilware extension:
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.

▼ Show Discussion