FIX: "Some settings are managed by your organization"
Get Free Scanner and check your computer for errors
Fix It NowTo fix found issues, you have to purchase the full version of Combo Cleaner. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
How to Fix the "Some settings are managed by your organization" Notification When Trying to Open Windows Defender
"Some settings are managed by your organization" is a Windows 10 notification. The notification does not explain how to solve the problem, but we will show you how to fix this issue in this article.
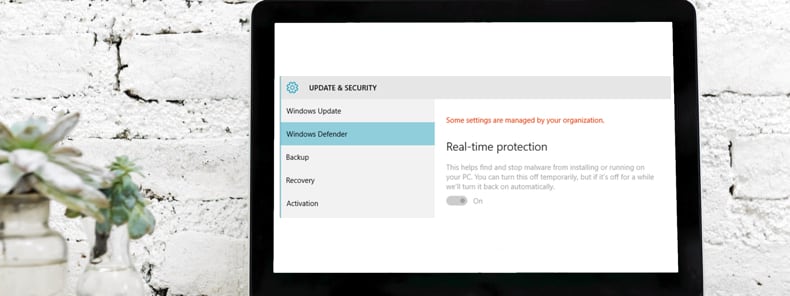
"Some settings are managed by your organization" appears when a Windows user tries to adjust settings to which they have limited access. Windows often includes packages that are configured by organizations to limit users' access to important settings. With the "Some settings are managed by your organization" notification, Windows blocks modification of settings to prevent possible damage to the Windows operating system or corruption of associated data.
Fortunately, it's possible to work around this notification and restore your ability to modify Windows settings. However, it can be time-consuming and requires some knowledge of Windows Registry Editor and Local Group Policy Editor.
In this guide, we thoroughly describe each step to make the process easier. Be aware that Local Group Policy Editor is not available in Windows Home edition. Registry Editor, on the other hand, will be available and might also help to solve the problem.
Video Showing How To Fix "Some settings are managed by your organization" Notification:
Table of Contents:
- Introduction
- Remove Windows Defender Policies Using Registry Editor
- Remove Windows Defender Policies Using Local Group Policy Editor
- Video Showing How To Fix "Some settings are managed by your organization" Notification
Download Computer Malware Repair Tool
It is recommended to run a free scan with Combo Cleaner - a tool to detect viruses and malware on your device. You will need to purchase the full version to remove infections. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Remove Windows Defender Policies Using Registry Editor
First, we recommend downloading a ZIP file (containing a REG file) that will help you easily remove Windows Defender policies.
Click this link, extract the REG file, and double-click it. Restart the computer for changes to take effect.
Now open the Registry Editor. To open Registry Editor, right-click the Start button and select "Run" from the contextual menu. Type "regedit" and press Enter or click "OK".
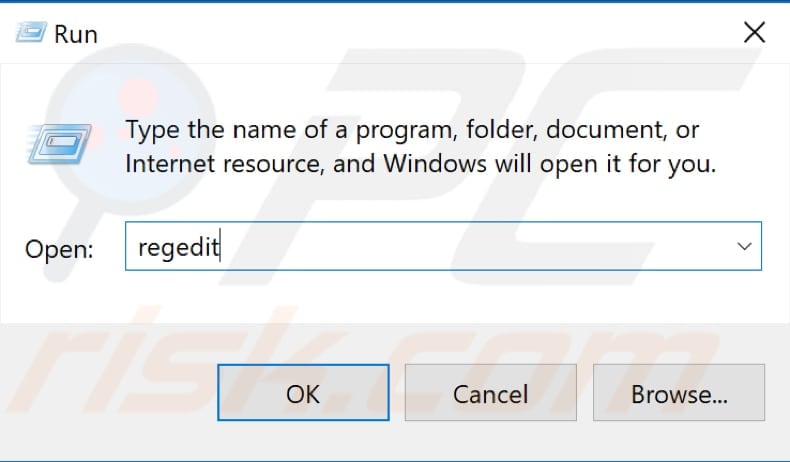
Follow this path: "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" (you can simply copy-and-paste it into the Registry Editor bar). Export this branch to a REG file by right-clicking it and selecting "Export". Select the location where do you want to place it and click "OK".
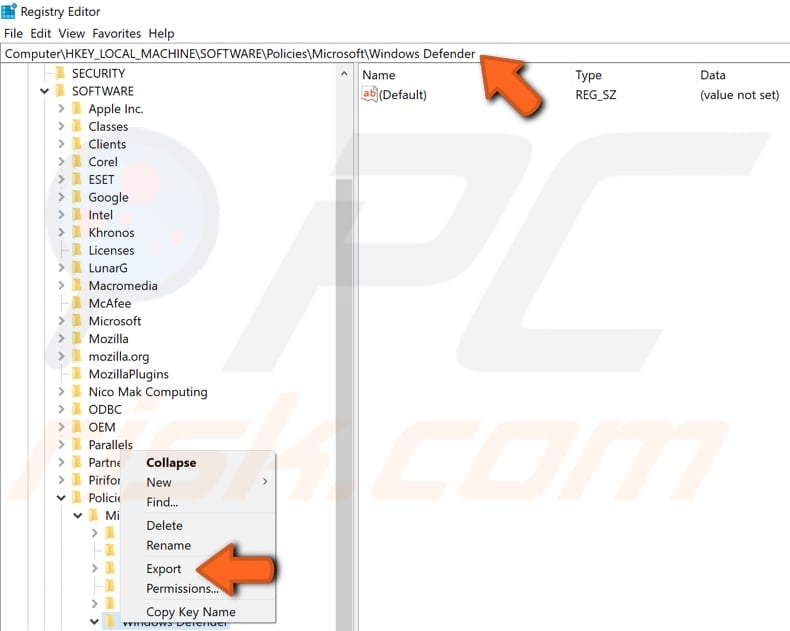
Now delete the same branch by right-clicking it and selecting "Delete".
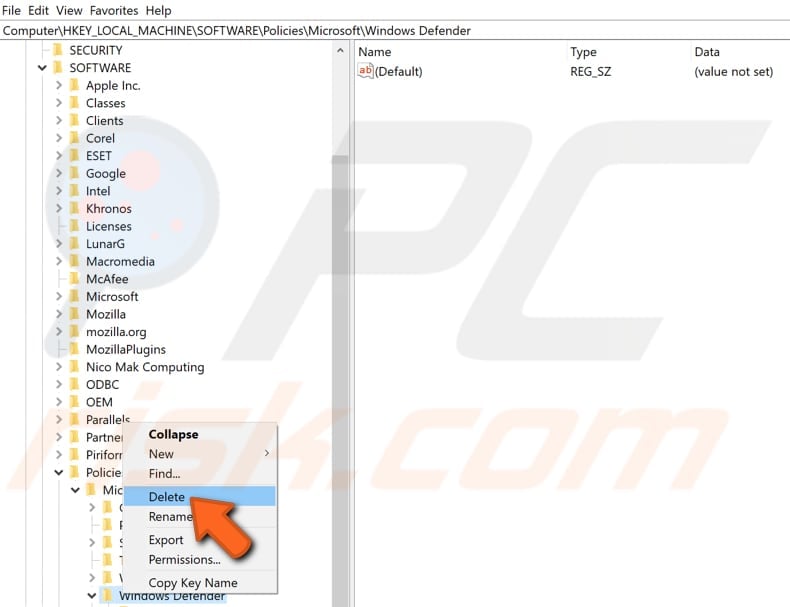
Repeat the steps with the branch you can find by following this path: "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Advanced Threat Protection".
Close Registry Editor and restart the computer. See if this fixes the problem. Windows should no longer show the "Some settings are managed by your organization" notification when you try to modify Windows Defender settings.
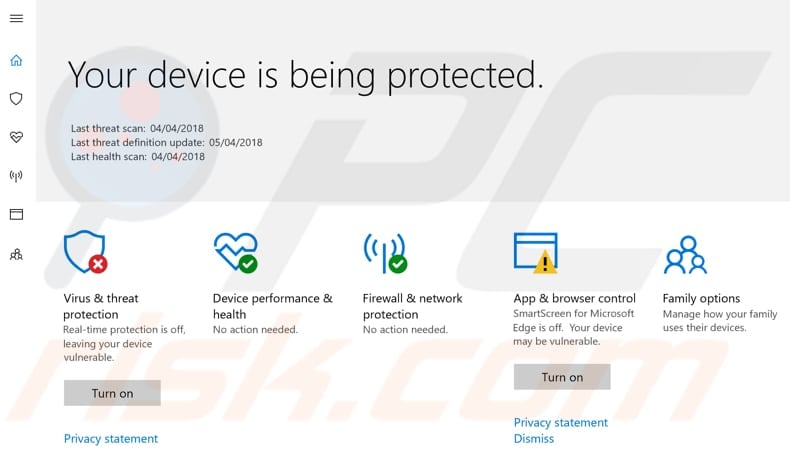
After removing Windows Defender policies, it will return to the state without limited access, and the Windows Defender Settings window should look like this:
Remove Windows Defender Policies Using Local Group Policy Editor
The Local Group Policy Editor (also known as gpedit.msc) is a Microsoft Management Console that allows you to manage Computer Configuration and User Configuration settings.
By default, the policies that are set in the Local Group Policy Editor apply to all Windows user accounts. As mentioned before, it is available only in Windows Pro, Enterprise, and Education editions, and not others such as Windows Home Edition.
Open Local Group Policy Editor by pressing the Windows (Win) key + R and typing "gpedit.msc", and then click "OK" or press Enter on the keyboard.
Follow this path in the right pane until you reach Windows Defender policies: "Computer Configuration/Administrative Templates/Windows Components/Windows Defender".
You will see a long list of policy settings with items in each sub-branch. Set each policy setting to "Not configured". This is the time-consuming part. Start with the following and ensure that all are set to "Not configured". If any policies are already set to "Not configured", enable them by right-clicking and selecting "Enable", and then set them back to "Not Configured":
- Allow antimalware service to startup with normal priority
- Turn off Windows Defender
- Configure local administrator merge behavior for lists
- Turn off routine remediation
- Define addresses to bypass proxy server
- Define proxy auto-config (.pac) for connecting to the network
- Define proxy server for connecting to the network
- Randomize scheduled task times
- Allow antimalware service to remain running always
Now, check the following ranges and also set their policy settings to "Not configured".
Windows Defender\Client Interface branch:
- Display additional text to clients when they need to perform an action
- Suppress all notifications
- Suppresses reboot notifications
- Enable headless UI mode
Windows Defender\Exclusions branch:
- Turn off Auto Exclusions
- Extension Exclusions
- Path Exclusions
- Process Exclusions
Windows Defender\MAPS branch:
- Configure the 'Block at First Sight' feature
- Join Microsoft MAPS
- Configure local setting override for reporting to Microsoft MAPS
- Send file samples when further analysis is required
Windows Defender\Network Inspection System branch:
- Turn on definition retirement
- Specify additional definition sets for network traffic inspection
- Turn on protocol recognition
Windows Defender\Quarantine branch:
- Configure local setting override for the removal of items from Quarantine folder
- Configure removal of items from Quarantine folder
Windows Defender\Real-time Protection branch:
- Turn off real-time protection
- Turn on behavior monitoring
- Scan all downloaded files and attachments
- Monitor file and program activity on your computer
- Turn on raw volume write notifications
- Turn on process scanning whenever real-time protection is enabled
- Define the maximum size of downloaded files and attachments to be scanned
- Configure local setting override for turn on behavior monitoring
- Configure local setting override for scanning all downloaded files and attachments
- Configure local setting override for monitoring file and program activity on your computer
- Configure local setting override to turn on real-time protection
- Configure local setting override for monitoring for incoming and outgoing file activity
- Configure monitoring for incoming and outgoing file and program activity
Windows Defender\Remediation branch:
- Configure local setting override for the time of day to run a scheduled full scan to complete remediation
- Specify the day of the week to run a scheduled full scan to complete remediation
- Specify the time of day to run a scheduled full scan to complete remediation
Windows Defender\Reporting branch:
- Configure time out for detections requiring additional action
- Configure time out for detections in critically failed state
- Configure Watson events
- Configure time out for detections in non-critical failed state
- Configure time out for detections in recently remediated state
- Configure Windows software trace preprocessor components
- Configure WPP tracing level
Windows Defender\Scan branch:
- Check for the latest virus and spyware definitions before running a scheduled scan
- Allow users to pause scan
- Specify the maximum depth to scan archive files
- Specify the maximum size of archive files to be scanned
- Specify the maximum percentage of CPU utilization during a scan
- Scan archive files
- Turn on catch-up full scan
- Turn on catch-up quick scan
- Turn on e-mail scanning
- Turn on heuristics
- Scan packed executables
- Scan removable drives
- Turn on reparse point scanning
- Create a system restore point
- Run full scan on mapped network drives
- Scan network files
- Configure local setting override for maximum percentage of CPU utilization
- Configure local setting override for the scan type to use for a scheduled scan
- Configure local setting override for schedule scan day
- Configure local setting override for scheduled quick scan time
- Configure local setting override for scheduled scan time
- Define the number of days after which a catch-up scan is forced
- Turn on removal of items from scan history folder
- Specify the interval to run quick scans per day
- Start the scheduled scan only when computer is on but not in use
- Specify the scan type to use for a scheduled scan
- Specify the day of the week to run a scheduled scan
- Specify the time for a daily quick scan
- Specify the time of day to run a scheduled scan
Windows Defender\Signature Updates branch:
- Define the number of days before spyware definitions are considered out of date
- Define the number of days before virus definitions are considered out of date
- Define file shares for downloading definition updates
- Turn on scan after signature update
- Allow definition updates when running on battery power
- Initiate definition update on startup
- Define the order of sources for downloading definition updates
- Allow definition updates from Microsoft Update
- Allow real-time definition updates based on reports to Microsoft MAPS
- Specify the day of the week to check for definition updates
- Specify the time to check for definition updates
- Allow notifications to disable definitions based reports to Microsoft MAPS
- Define the number of days after which a catch-up definition update is required
- Specify the interval to check for definition updates
- Check for the latest virus and spyware definitions on startup
Windows Defender\Threats branch:
- Specify threats upon which default action should not be taken when detected
- Specify threat alert levels at which default action should not be taken when detected
We hope that one of these solutions (depending on the edition of your operating system) solves the problem and you no longer receive the "Some settings are managed by your organization" notification when trying to modify Windows Defender settings. If you know of other methods to solve the problem not mentioned in our guide, please share them with us by leaving a comment in the section below.
Share:

Rimvydas Iliavicius
Researcher, author
Rimvydas is a researcher with over four years of experience in the cybersecurity industry. He attended Kaunas University of Technology and graduated with a Master's degree in Translation and Localization of Technical texts. His interests in computers and technology led him to become a versatile author in the IT industry. At PCrisk, he's responsible for writing in-depth how-to articles for Microsoft Windows.

▼ Show Discussion