What Is Malware and How to Remove It?
Get Free Scanner and check your computer for errors
Fix It NowTo fix found issues, you have to purchase the full version of Combo Cleaner. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
What Is Malware and How to Manually Remove It From Your Computer
Malware (Malicious software) is any program or file that is harmful to a computer and user. Removing it is paramount, but it's often not easy. This article will show you how to remove malware manually.

Malware includes computer viruses, worms, Trojan horses, spyware, and ransomware, each with its unique characteristics. These malicious programs perform many functions, including stealing, encrypting, or deleting sensitive data, altering or hijacking core computing functions, and monitoring users' computer activity without permission.
Most types of malware are easily removable. They are programs like any other legitimate software you might use. Therefore, you can uninstall them from the Windows operating system like any other program.
However, not all types of malware are this easily removed. Some can only be removed manually. This article provides information about different types of malware and how you can remove most of these infections from your computer.
Video Showing How to Remove Malware Manually:
Table of Contents:
- Introduction
- What Is Adware
- What Is Ransomware
- What Is Spyware
- What Is Trojan
- What Is Worm
- What Is Virus
- What Is Tech Support Scam
- Anti-virus And Anti-Malware Programs
- How To Remove Infections Manually
- Video Showing How To Remove Malware Manually
Download Computer Malware Repair Tool
It is recommended to run a free scan with Combo Cleaner - a tool to detect viruses and malware on your device. You will need to purchase the full version to remove infections. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
What Is Adware
Adware is any software application in which advertising banners are displayed while a program is running. The advertisements are delivered through pop-up windows or bars that appear on the program's user interface. Adware is commonly created for computers but may also be found on mobile devices. Not all adware programs are malware. There are many free authorized programs containing adware, and this is often how revenue is generated for the developers. You might receive a free program or app, but the 'price' you pay is that it contains ads.
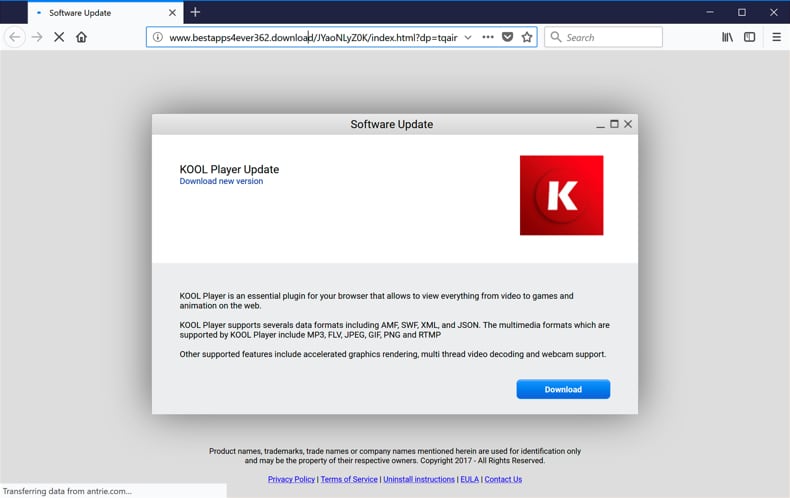
What Is Ransomware
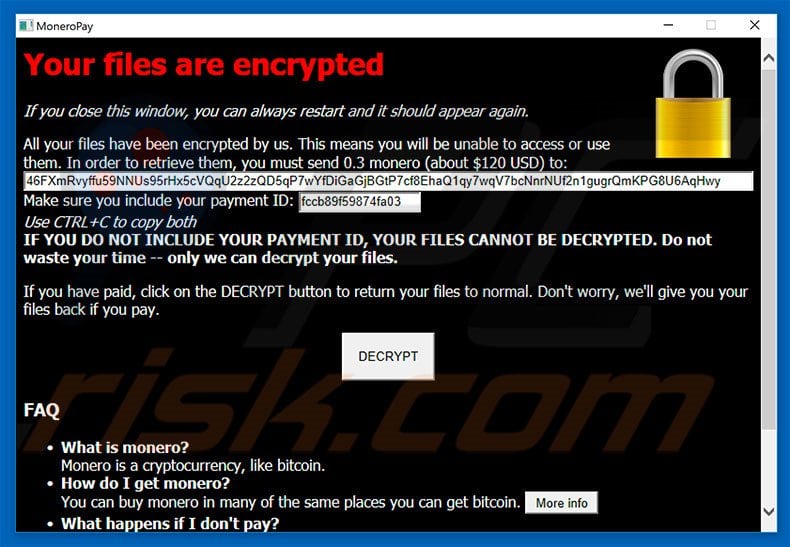
Ransomware is very different from adware, can be very harmful, and is one of the biggest problems on the Internet these days. Ransomware restricts access to data by encrypting files or locking computer screens. It then attempts to extort money from victims by demanding ransom payments, usually in cryptocurrencies such as Bitcoin, in exchange for access to their data. This infection often begins when users click on something that initially appears innocuous, such as an attachment. Some of us receive hundreds of emails daily, often needing to download and open attachments, and therefore, these attachments can sometimes be downloaded without due care. If you are running a business, this could have devastating consequences. Being locked out of your own files by malware for even just a day can greatly impact revenue.
What Is Spyware
Spyware is a type of malware that is often hard to detect. It collects information about your Internet browsing habits, browsing history, or personal information (such as credit card numbers). It commonly uses the Internet to pass this information on to third parties without your knowledge. Spyware is often tied up with other software or downloads on file-sharing sites. For example, free music or movie download sites. It can also be installed when opening an email attachment.
Due to its secretive nature, spyware can go unnoticed - most people are not aware that spyware is on their systems, especially if it is not protected by an anti-spyware program. If you see new or unidentified icons in the taskbar at the bottom of your screen, are redirected to a different search engine while searching, or random error messages appear while performing various operations (that previously worked fine), then your computer is probably infected with spyware.
What Is Trojan
In computing, a Trojan horse (or Trojan) is any malicious computer program that misleads users of its true intent. Trojans can be used by cyber thieves and hackers trying to gain access to users' systems. Once Trojans are activated, they can enable cyber-criminals to spy on you, steal your sensitive data, and gain 'backdoor' access to your system. These actions can include deleting your data, blocking it, modifying and copying it, disrupting computer performance or whole computer networks.
Trojans are not just problems for laptop and desktop machines only - they can also affect your mobile devices. Generally speaking, Trojans are attached to what appear to be legitimate programs. In fact, they are fake versions loaded with malware.
What Is Worm
A computer worm is a type of malicious software whose primary function is to infect other computers by duplicating itself while remaining active on infected systems. It can spread itself on other computers without being activated by users. Some types of worms spread by sending themselves to each contact on your email address book and then to all of the contacts on the address books of the recipients. Thus, worms are capable of proliferating themselves to many computers within hours.
Worms hide in areas of the operating system that are often invisible to regular users. It becomes obvious that there is a worm on your computer when it starts to consume considerable system resources - it will start to slow down or suspend various tasks. If there are new icons or shortcuts on your desktop, or you receive pop-ups regularly, this could also mean that your operating system is infected by a computer worm.
What Is Virus
A computer virus is a malicious software program that replicates by copying itself to another program, computer boot sector, or document and then changes how a computer functions. Viruses never occur naturally. They are always induced by people. Not all computer viruses are destructive.
However, most perform actions that are malicious in nature, such as destroying/deleting data, overwriting information, and displaying messages. Viruses do not physically harm the computer system or hardware. A computer can be infected by a virus when downloading files from unknown or untrusted sources. Downloading email attachments from unknown senders can also infect your computer with viruses.
What Is Tech Support Scam
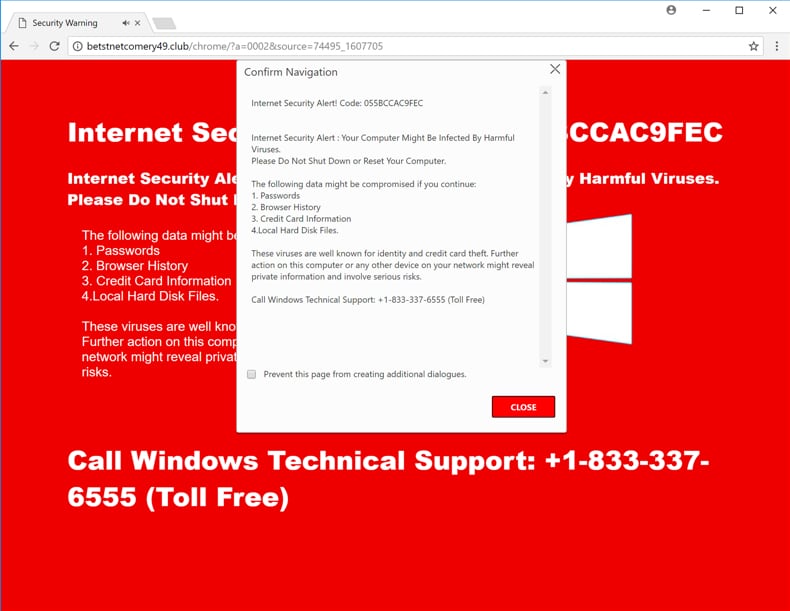
A technical support scam refers to telephone fraud activities in which scammers claim to offer legitimate technical support services, often via cold calls to unsuspecting users. These cold calls are mostly targeted at Microsoft Windows users, with the caller claiming to represent a Microsoft technical support department.
They usually start with a fake alert stating that there is a problem with your computer. They then threaten to lock you out of your operating system until you call a telephone number provided. Once you call the number, the scammers try to sell you remote technical support services and software.
Anti-virus And Anti-Malware Programs
Today, having anti-virus or anti-malware software installed on your Windows is imperative. Furthermore, ensure that you have the software installed and updated with the latest definitions. If you do not have an anti-virus or anti-malware program installed on your computer, or you want to try alternative software to protect you from malware, here is a list of programs that we recommend:
Restoro PC Repair Tool
Restoro is a company fast becoming a world leader within the IT sector. Key to their ambition is their flagship product, Restoro PC Repair Solution, first made available to the public in 2007. The program is advertised as “Windows Problem Relief” and is designed primarily to scan, assess, and repair files within the operating system. In addition, files rendered corrupt by various malware infections are restored to their original state, thus ensuring stability and a return to efficient system operation.
Restoro was premised on the idea that, through a dedicated team of professionals, they could create software that not only provides the features above but is also affordable and simple to use. Since 2007, the company has won numerous awards.
Despite the awards and the accolades already received, they remain dedicated to providing a solid, dependable product with their R&D team working continuously to ensure compatibility with every new Windows build and Microsoft security patch. You can download it here.
Bullguard
BullGuard make it simple to protect everything in your digital life — from your data to your identity to your Smart Home. As the only security company whose sole focus is on the consumer, BullGuard combines technical expertise with a genuine understanding of your needs to deliver complete protection across all connected devices.
BullGuard is your own private bodyguard — tracking and tackling security threats so you can connect confidently, control easily, and travel freely throughout your digital world. You can download BullGuard here.
Bitdefender
Bitdefender is led by a vision to be the most trusted cybersecurity technology provider globally, which means they are constantly anticipating, innovative, and going the extra mile. Bitdefender delivers robust security you can rely on. With a global security delivery infrastructure protecting half a billion users, visionary solutions, and a wealth of awards, Bitdefender has been a trusted security provider since 2001.
They work with government organizations, large enterprises, SMEs, and private individuals across more than 150 countries. They are dedicated to providing solutions to each of their challenges and needs – and their dedication proves to be successful. You can download Bitdefender here.
ESET NOD32
ESET began life as a pioneer of antivirus protection, creating award-winning threat-detection software. Now, ESET's goal is to make sure that everybody can enjoy the breathtaking opportunities that technology offers.
ESET's security solutions allow businesses and consumers in more than 200 countries and territories to make the most of the digital world. You can download ESET NOD32 Antivirus here.
Kaspersky
Kaspersky Antivirus is a stripped-back security package that focuses on core security essentials: web filtering blocks dangerous URLs, an accurate antivirus engine detects and removes threats, and smart monitoring technologies track and reverse malicious actions.
Kaspersky is amongst the best software at blocking malware and removing it from an infected system. You can download it here.
Norton
Norton Antivirus is a top-quality malware hunter that can automatically protect your computer. It also offers many tweaks, options, and settings, making it one of the best antivirus software suites currently available.
It is easy to use, has configuration options for advanced users, comes highly rated by the testing labs, and is carefully designed to have the least possible impact on system performance. You can download it here.
Windows Defender
We should not forget Windows Defender, an antivirus program fully integrated part of Windows 10. It offers real-time protection from various threats such as adware, spyware, and viruses. Windows Defender is fast and light and does not consume too many system resources.
Windows Defender is one of the most widely-used antivirus programs. It uses signature-matching scanning to compare potential viruses against a database of known threats to protect your computer.
It also uses analysis, which monitors software and other attributes to detect new malware and malware that is rapidly changing its code to avoid detection. Everything that appears suspicious is sent to Microsoft for further analysis. We recommend that you use all of the features provided to stay fully protected. This one is a good solution for those who prefer free security solutions.
We also recommend that you install and scan your computer with anti-malware programs. It takes less time to update them, and, furthermore, anti-malware programs target more adware and unwanted programs than anti-virus software. We recommend the following anti-malware programs:
Malwarebytes
Malwarebytes is an American Internet security company. By 2015, Malwarebytes had fixed over 250 million computers and over five billion malware threats worldwide.
Malwarebytes Anti-Malware is available in two versions, one for free download for home computers and the other a professional version, with a 14-day free trial in advance. You can download it here.
Spybot
Spybot - Search & Destroy is a free Internet security program provided by Safer-Networking Ltd, specializing in removing malware, spyware, and adware to ensure that files and data are kept secure and private.
With thousands of downloads each day, Spybot has become one of the most popular anti-malware programs on the Internet. You can download Spybot here.
Emsisoft
Emsisoft Anti-Malware focuses on the core task of keeping your computer free of malware. It does a good job, and with a clean, simple interface, it looks good too. They are offering innovative anti-malware solutions that are efficient, powerful, unobtrusive, and minimalistic. You can download it here.
How To Remove Infections Manually
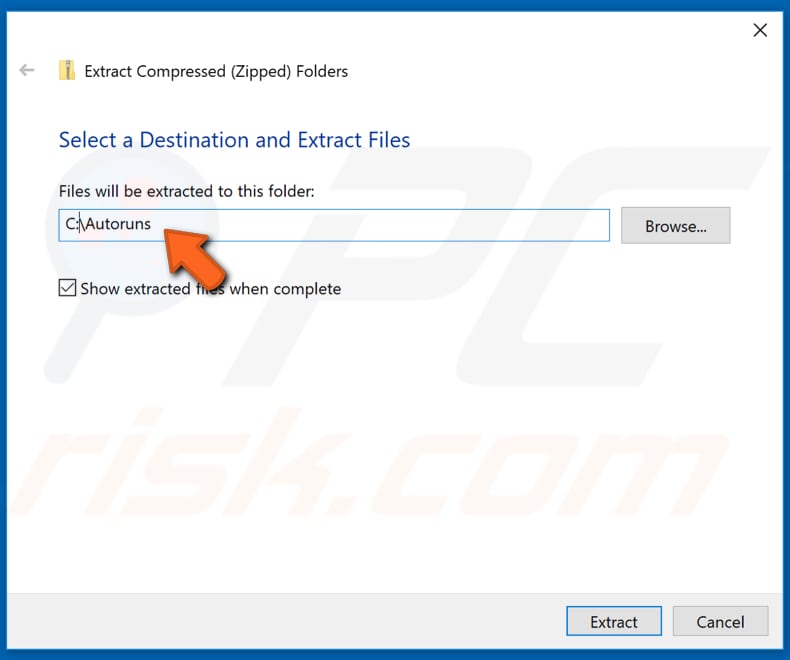
If you have tried anti-virus or anti-malware programs, you believe that malware remains on your computer, and none of the anti-malware tools are detecting it, then you should try to remove it manually. In this guide, we show how to remove programs that you suspect are infected with malware. First, download the Autoruns program and extract it to C:\Autoruns. You can download Autoruns here.
Reboot Windows into Safe Mode. This will prevent malware from starting when going through these steps. Many malware infections monitor keys that allow them to start. If they detect they have been removed, they will automatically replace the startup key.
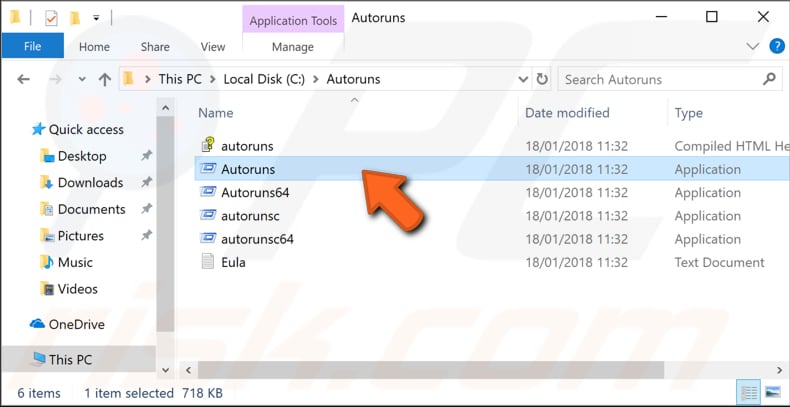
In Safe Mode, go to the "C:\Autoruns" folder that you created previously and double-click "Autoruns."
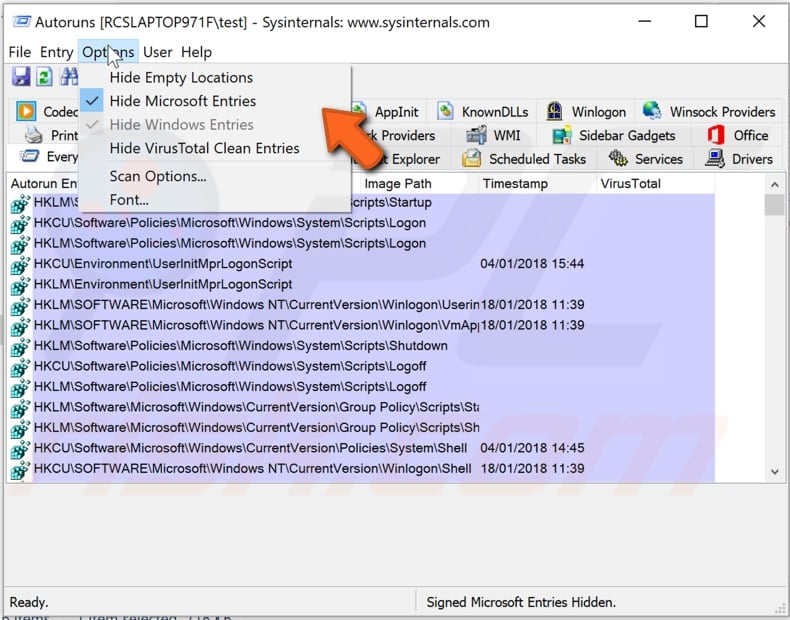
When the program starts, click on the "Options" menu and disable "Hide Empty Locations," enable "Hide Microsoft Entries," and enable the "Verify Code Signatures" (in "Scan Options..." under Options) options by clicking them. This will place (or remove) a checkmark beside each of these options. Then press the F5 key on your keyboard to refresh the startups list using these new settings.
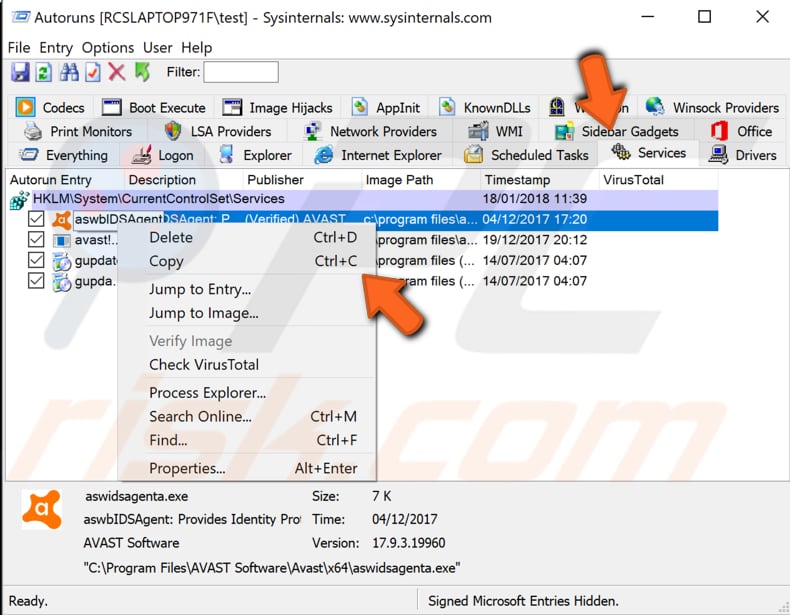
The program shows information about your startup entries in several different tabs. The filename you are looking for will generally be found under the "Logon" or "Services" tabs, but check the other tabs as well. Click each tab and look through the list for the filename you wish to remove. The filename will be found under the "Image Path" column.
Note that many malware programs are disguised by using the same filenames as valid Microsoft files. You need to know exactly which files you wish to remove and in which folder they reside. Once you find the entry you believe is associated with the malware, right-click on the entry and select delete. This startup entry will now be removed from the Registry.
Now that the program will not start on boot up, you should delete the file through File Explorer. If you can not see the file, it may be hidden. To see hidden files on Windows 10, go to File Explorer and click the View tab, and then click "Options."
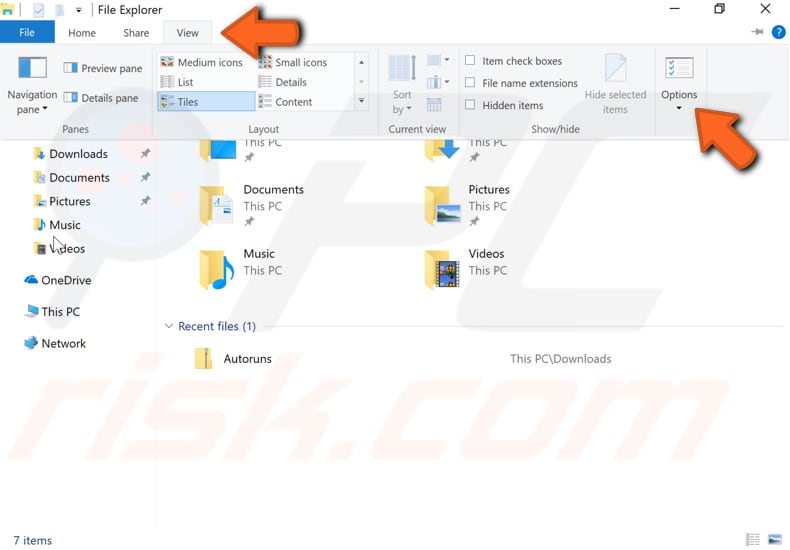
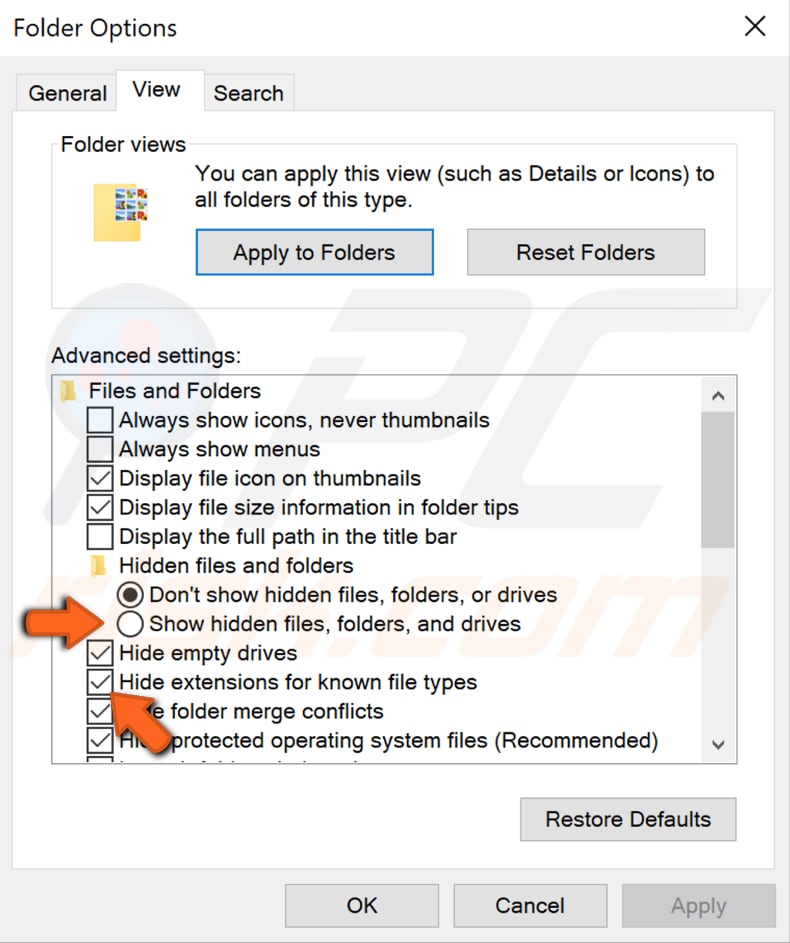
In the Folder Options window, click the "View" tab and then enable the "Show hidden files, folders, or drives" option and remove the checkmark from the checkbox named "Hide extensions for known file types." Click "Apply" and "OK" when finished to save the changes made.
When you have finished removing malware entries from the Registry and deleting files, reboot into Normal Mode. Your computer should now be clean from infections.
We hope this guide helps you find the best anti-virus or anti-malware program to make your computer infection-free!
Share:

Rimvydas Iliavicius
Researcher, author
Rimvydas is a researcher with over four years of experience in the cybersecurity industry. He attended Kaunas University of Technology and graduated with a Master's degree in Translation and Localization of Technical texts. His interests in computers and technology led him to become a versatile author in the IT industry. At PCrisk, he's responsible for writing in-depth how-to articles for Microsoft Windows.

▼ Show Discussion