Petya Ransomware
What is Petya?
Petya is ransomware distributed via malicious e-mails containing Dropbox download links to applications which, when executed, will install Petya on victims' computers. Research shows that these e-mails mainly target human resources (HR) departments of various German companies. After system infiltration, Petya encrypts portions of hard drives and makes ransom demands.
Download Computer Malware Repair Tool
It is recommended to run a free scan with Combo Cleaner - a tool to detect viruses and malware on your device. You will need to purchase the full version to remove infections. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
By encrypting hard drive portions, Petya prevents users from booting their operating systems. The ransomware replaces the Master Boot Record (information placed at the beginning of hard drive instructs the computer how to boot) with a malicious loader. Petya then automatically restarts the computer. Once the computer is rebooted, the new (malicious) loader will execute and begin encrypting files. During this process, a fake check disk (CHKDSK) screen is shown. The ransomware corrupts the Master File Table (MFT). Therefore, the computer is unable to reference the location of files on the system (if there are any). Files become inaccessible, and therefore, Windows can no longer load. An image of a skull is then displayed, which changes to a lock screen containing a message claiming that the files have been encrypted and the victim must pay a ransom to restore them. The screen encourages users to download the Tor browser and visit URLs provided that supposedly contain further payment instructions. Research shows that there is no way to restore the files without payment. You can repair your MBR, and although this will remove the lock screen, it will not decrypt the files - it will only provide an opportunity to format the hard drive and install a new copy of Windows. Again, at time of research, there were no tools capable of decrypting the Master Boot Record to make files accessible.
Screenshot of Petya ransomware website:
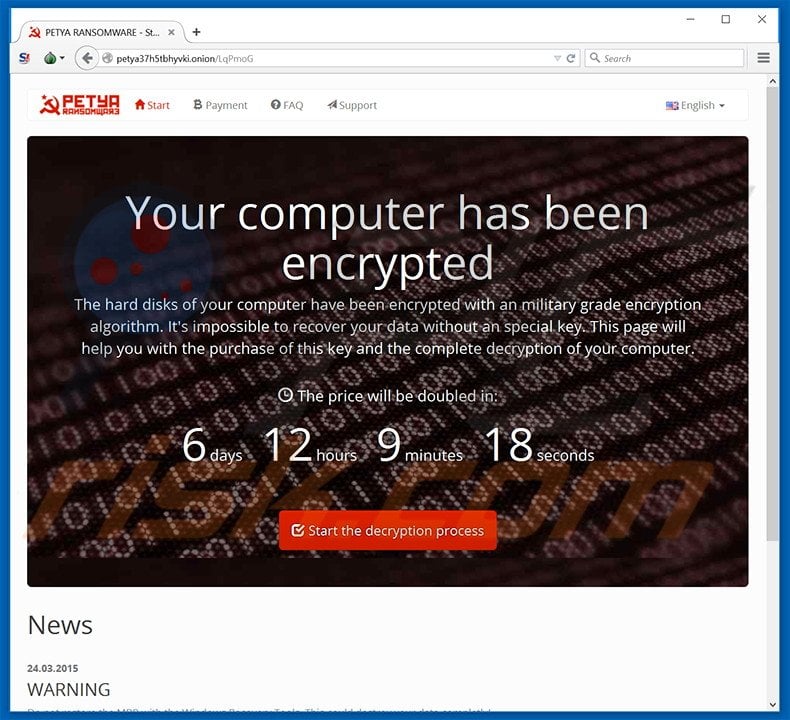
Although encrypting portions of hard drives in this manner is quite unique, ransomware-type viruses tend to have similar behavior. Locky, TeslaCrypt, Converton, and Rokku, Maktub are just some examples from a long list of similar ransomware infections. All encrypt files and make ransom demands. Most use asymmetric encryption. The average size of ransoms is 1~ Bitcoin (at time of research, equivalent to $413.75). Furthermore, many of these viruses are proliferated using fake software updates, trojans, peer to peer (P2P) networks, and/or malicious email attachments. Therefore, express caution when downloading apps/files from third party sources. Ensure that email attachments that you are opening are sent from trusted addresses. Keeping your installed software up-to-date and using a legitimate anti-spyware/anti-virus suite is also paramount.
Update 25 July, 2017 - Security researchers from Malwarebytes used a released master key for this ransomware and were able to develop a decrypter. You can read more about it HERE.
Text presented on the Petya ransomware website:
Your computer has been encrypted.
The hard disks of your computer have been encrypted with a military grade encryption algorithm. It’s impossible to recover your data without a special key. This page will help you with the purchase of this key and the complete decryption of your computer.
Petya ransomware website Frequently Asked Questions (FAQ):
Petya fake Check Disk (CHKDISK) screen:
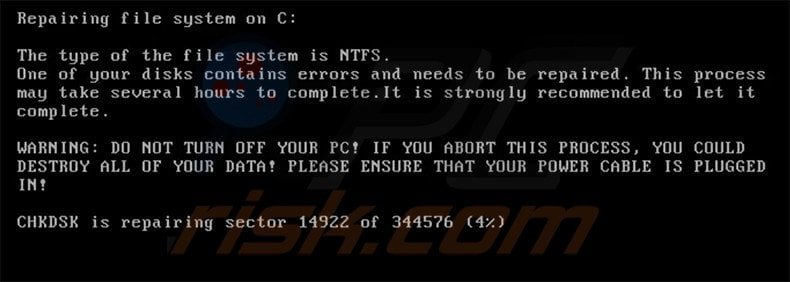
Text presented within this screen:
Repairing file system on C:
The type of the file system is NTFS.
One of your disks contains errors and needs to be repaired. This process may take several hours to complete. It is strongly recommended to let it complete.
WARNING: DO NOT TURN OFF YOUR PC! IF YOU ABORT THIS PROCESS, YOU COULD DESTROY ALL OF YOU DATA! PLEASE ENSURE THAT YOUR POWER CABLE IS PLUGGED IN!
CHKDSK is repairing sector --- of ---- (-%)
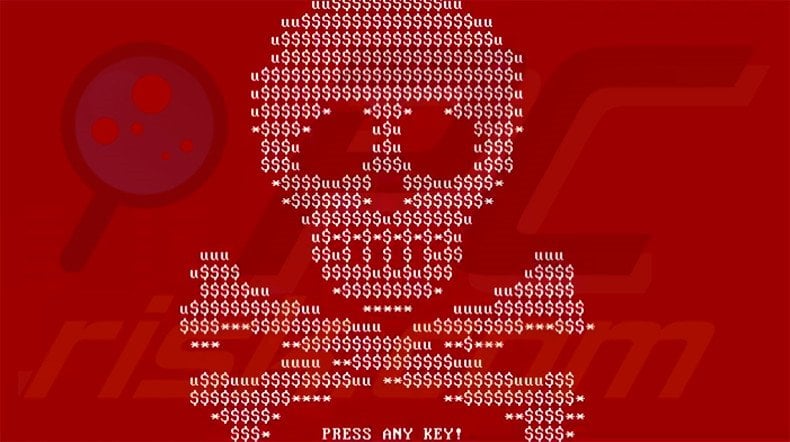
Screenshot of a skull image displayed by Petya ransomware:
Screenshot of Petya ransomware lock screen:
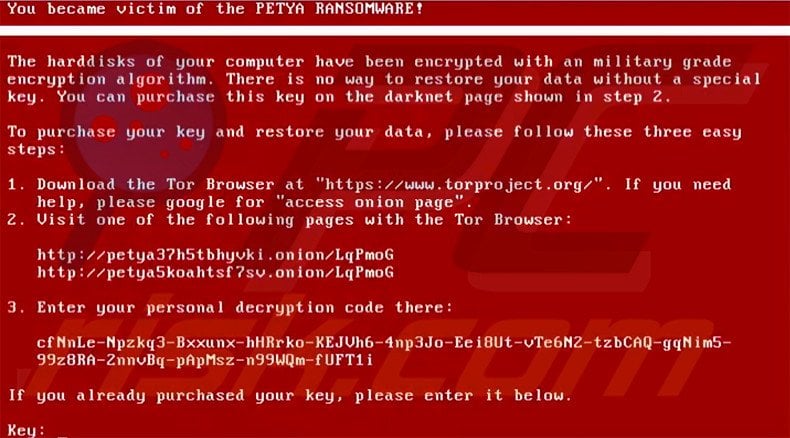
Text presented within the lock screen:
You became victim of the PETYA RANSOMWARE!
The hard disks of your computer have been encrypted with a military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download the Tor browser at “https://www.torproject.org/“.
2. Visit one of the following pages with the Tor Browser:
http://petya37h5tbhyvki.onion/LqPmoG
3. Enter you personal decryption code there:
If you already purchase your key, please enter it below.
Key:
Update 11 April, 2016 - Security researchers were able to develop a tool that can decrypt files compromised by Petya ransomware for free. To use this tool (created by leostone) you should disconnect the hard drive containing files encrypted by Petya ransomware and connect it to another computer. Then you could use a tool developed by Fabian Wosar to get your disk’s data needed to generate a password to decrypt the files. After connecting the HDD to the clean computer your should launch the PetyaExtractor.exe program. Then navigate to https://petya-pay-no-ransom.herokuapp.com (if not available try - https://petya-pay-no-ransom-mirror1.herokuapp.com/) website. In Petya Sector Extractor program click “Copy Sector” button then navigate to the petya-pay-no-ransom website and paste it to “Base64 encoded 512 bytes verification data” field. Then go back to Petya Sector Extractor program and click “Copy Nonce” button, navigate to petya-pay-no-ransom website and paste it to “Base64 encoded 8 bytes nonce” field. Now you should click “Submit” button in the website and wait for a few moments to receive your password. You should write it down, connect the HDD to the original computer, when you see the Petya ransom lock screen you should enter the password that you previously wrote down. If everything was done correctly your data should be decrypted.
Update 12 May, 2016 - Cyber criminals have updated Petya ransomware. It now uses a green/black colour scheme instead of white/red. Further updates include the use of a secondary ransomware called “Mischa”. This ransomware is installed on victim’s computer if the user doesn’t grant the administrative rights when executing an infected email attachment.
Screenshots of an updated Petya ransomware:
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.


▼ Show Discussion