How to Remove “Your device has been blocked” Ransomware Virus from Android Tablet or Phone?
"Your device has been blocked" - How to Remove Ransomware Infections From an Android Device?
Cybercriminals have been spreading ransomware viruses on Windows-based computers for some time. These infections became popular in mid-2006 and continue to infect personal computers and extort money from their victims.
Recently, security research began showing a rise in Android-based mobile ransomware infections. Usually, ransomware viruses exploit the names of authorities, including the FBI, USA Cyber Crime Investigations, and The ICE Cyber Crime Center - making fake claims that users must pay an amount of money (for supposed law violations such as watching pornography, using copyrighted files, etc.) to unblock their devices.
In most cases, cybercriminals employ the Green Dot MoneyPak, Ukash, or PaySafeCard pre-paid card services to collect fake fines from unsuspecting mobile device users. Tablet and mobile phone users should be aware that paying these fines as ordered by these messages is equivalent to sending their money to cybercriminals.
Note that neither the FBI nor any other authority use screen lockers to collect any fines.

Cybercriminals have localized ransomware viruses that target mobile devices. Therefore, users from different countries see fake screen-locking messages displayed in their local language and exploit authorities' names from their countries.
Ransomware infections have become a profitable business for cybercriminals who continue to search for various ways of infecting mobile devices worldwide. At the time of writing, some ransomware viruses were targeting Android devices - all using rogue applications to lock tablet or phone screens.
Koler Android Ransomware:
Distributed using fake applications (for example, "BaDoink" and "PhotoViewer").
Other known variants of this ransomware are proliferated using text message spam. An infected mobile device sends an SMS message to all contacts in the address book ("Someone made a profile named 'contact's name' and he uploaded some of your photos! is that you?") followed by a link leading to a Dropbox page.
Android device users who follow this link will inadvertently download a "PhotoViewer" application, launching the screen-locking message.

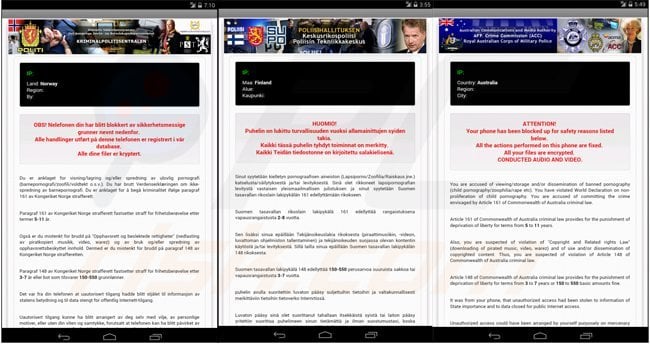
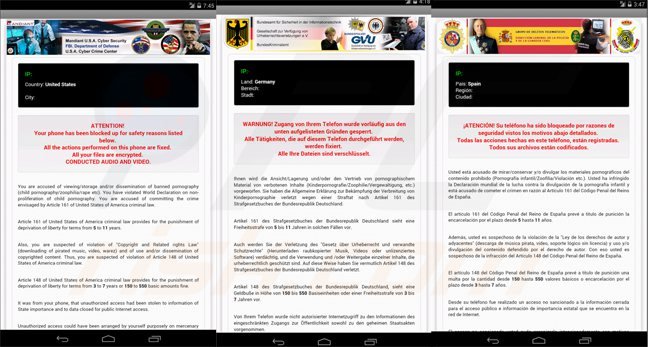
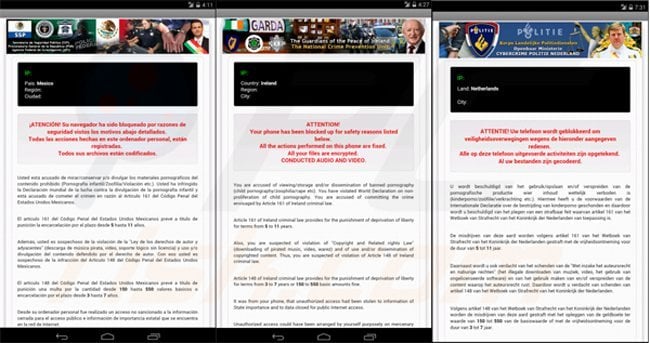
Screenshots of mobile devices locked by the Koler ransomware virus targeting different counties (Koler Android ransomware Trojan - demanding a payment of $300 using MoneyPak, PaySafeCard, or Ukash):
Norway: KRIMINALPOLITISENTRALEN - OBS! Nelefonen din har blitt blokkert av sikkerhetsmessige grunner nevnt nedenfor.
Finland: POLIISIHALLITUKSEN - HOUMIO! Puhelin on lukittu turvallisuuden vuoksi allamainittujen syiden takia.
Australia: AFP. Crime Commision (ACC) - ATTENTION! Your phone has been blocked up for safety reasons listed below.
USA: Mandiant U.S.A. Cyber Security FBI. Department of Defense - Your Phone has been blocked up for safety reasons listed below.
Spain: GRUPO DE DELITOS TELEMATICOS - Atención! Su teléfono ha sido bloqueado por razones de seguridad vistos los motivos abajo detallados.
Germany: - BUNDESPOLIZEI, GVU - WARNUNG! Zugang von Ihrem Telefon wurde vorläufig aus den unten aufgelisteten Gründen gesperrt.
Ireland: GARDA, The Guardians of the Peace of Ireland - Your Phone has been blocked up for safety reasons listed below.
Mexico: SSP - Atención! Su teléfono ha sido bloqueado por razones de seguridad vistos los motivos abajo detallados.
Netherlands: - ATTENTE! Uw telefoon wordt geblokkeerd om veiligheidsoverwegingen wegens de hieronder aangegeven redenen.
Switzerland: FEDPOL. BundesKriminalPolizei - WARNUNG! Zugang von Ihrem Telefon wurde vorläufig aus den unten aufgelisteten Gründen gesperrt.
United Kingdom: PCeU, Metropolitan British Police - ATTENTION! Your phone has been blocked up for safety reasons listed below.
Poland: Polizja Biuro Służby Kryminalnej - Panska telefon zostal zablokowany ze wzgledow bezpieczenstwa z wskazanych nizej przyczyn.
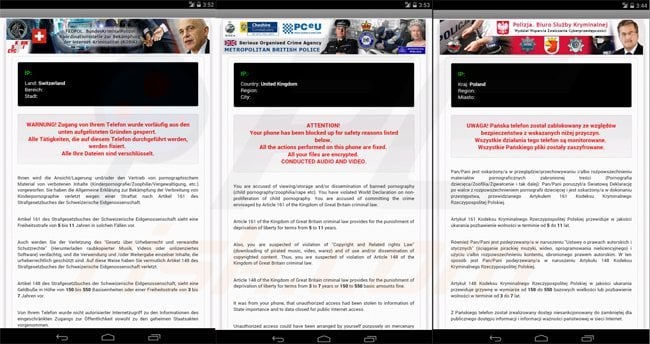
France: POLICE NATIONALE - ATTENTION! Votre telephone est bloque des raisons de sécurité suivantes.
New Zealand: New Zealand E-crime Lab - ATTENTION! Your phone has been blocked up for safety reasons listed below.
Portugal: POLICIA JUDICIARIA DE PORTUGAL - ATENÇÃO! O seu telefone esta bloqueado por razoes de segurança, pelas seguintes razoes.
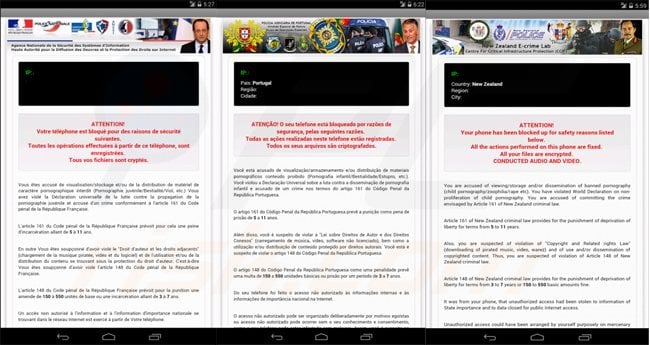
Slovakia: Policajnehi Zboru - VAROVANIE! Vas telefon je uzamknuty z bezpecnostnych dovodov by z nasledujucich dovodov.
Slovenia: NACIONALNI PREISKOVALNI URAD - POZOR! Vas spletni telefon je blokiran iz varnostnih razlogov nizje.
Turkey: JANDARMA GENEL KOMUTANLIGI - DIKKAT! Telefon guvenlik hususunda asagidaki nedenlerle bloke edilmis.
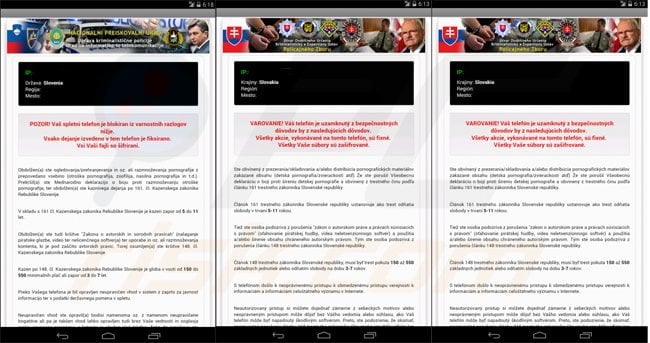
Text presented in Koler Android ransomware virus:
Mandiant U.S.A. Cyber Security
FBI Department Defense
U.S.A Cyber Crime CenterATTENTION! Your phone has been blocked up for safety reasons listed below. All the actions performed on this phone are fixed. All your files are encrypted. CONDUCTED AUDIO AND VIDEO. You are accused of viewing/storage and/or dissemination of banned pornography (child pornography/zoophilia/rape etc.) You have violated World Declaration on non-proliferation of child pornography. You are accused of committing the crime envisaged by Article 161 of United States of America criminal law. The penalty set must be paid in course of 48 hours as of the breach. On expiration of the term, 48 hours that follow will be used for automatic collection of data on yourself and your misconduct, and criminal case will be opened against you. Amount of fine is 300$. You can settle the fine with MoneyPak xress Packet vouchers. As soon as the money arrives to the Treasury account, your phone will be unblocked and all information will be decrypted in course of 24 hours.
FBI Android Ransomware Virus:
Distributed using a fake Android application named "Porndroid".
Users who install this fake app are presented with a ransom-demanding notification (false accusations of viewing child pornography).
Screenshot of a mobile device locked by FBI Android ransomware virus (demanding a payment of $500 using MoneyPak):
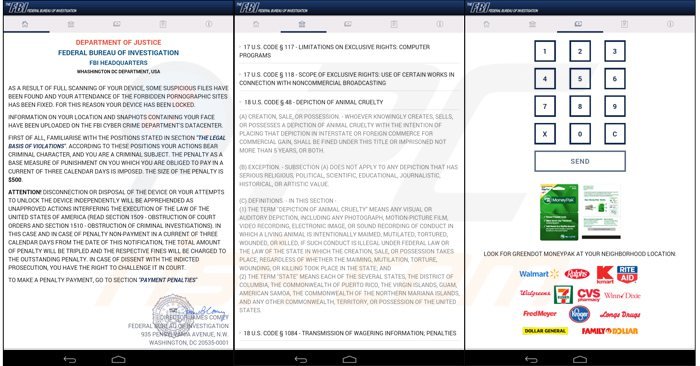
Text presented in FBI Android ransomware virus:
DEPARTMENT OF JUSTICE
FEDERAL BUREAU OF INVESTIGATION
FBI HEADQUARTERS
WASHINGTON DC DEPARTMENT, USAAs a result of full scanning of your device, some suspicious files have been found and your attendance of the forbidden pornographic sites has been fixed. For this reason your device has been locked. Information on your location and snapshots containing your face have been uploaded on the FBI Cyber Crime Department’s data center. First of all, familiarize with the positions stated in the section “The Legal Basis of Violations”. According to these positions your actions bear criminal character, and you are a criminal subject. The penalty as a base measure of punishment on you which you are obliged to pay in a current of three calendar days is opposed. The size of the penalty is $500
Attention! Disconnection of disposal of the device or your attempts to unlock the device independently will be apprehended as unapproved actions interfering the execution of the law of the United States of America (read section 1509 - obstruction of court orders and section 1510 - obstruction of criminal investigations). In this case and in case of penalty non-payment in a current of tree calendar days from the date of this notification, the total amount of penalty will be tripled and the respective fines will be charged to the outstanding penalty. In case of dissent with the indicted prosecution, you have the right to challenge it in court. To make a penalty payment, go to section “Payment Penalties”.
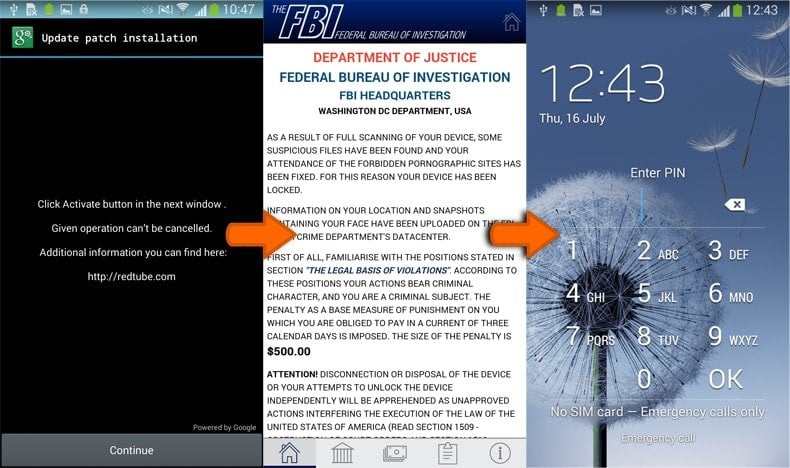
Update - 14 September 2015 - Another ransomware variant can change victims' PIN for the lock screen. The malware is spread through fake adult videos that install a rogue application called "Porn Droid" on the victim's device. After successful infiltration, this malicious app gains Device Administrator privileges by tricking users into installing a fake update patch.
After gaining administrator privileges, this ransomware presents its victims with a fake message which supposedly was sent by the FBI demanding to pay a fine of $500 for watching forbidden pornographic sites. Moreover, it changes the PIN lock of the compromised device. To remove the PIN lock, users should reset their devices to factory defaults.
Update 13 April 2016 - A new ransomware called Sonorousness started attacking Android users. Cybercriminals are using the name Cyber.Police to trick mobile users into paying a fake fine for supposedly watching illegal pornography.
This ransomware installs on the victim's device by impersonating an application that supposedly delivers porn media.
Screenshot of Sonorousness ransomware:
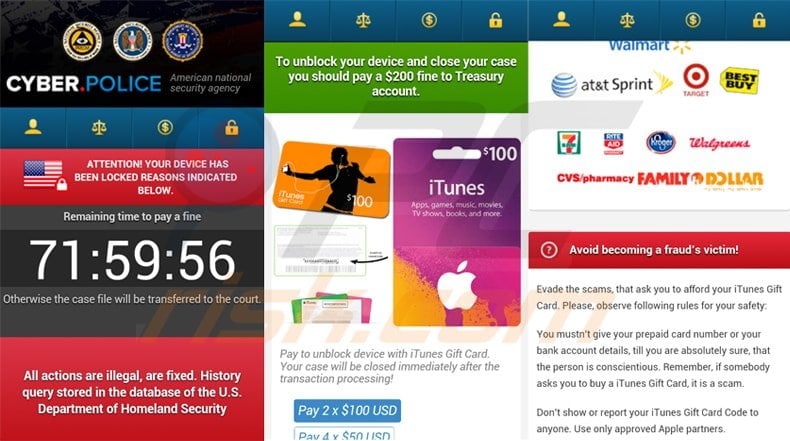
Text presented in this ransomware:
CYBER.POLICE American national security agency
ATTENTION! YOUR DEVICE HAS BEEN LOCKED REASONS INDICATED BELOW. Remaining time to pay a fine. Otherwise the case file will be transferred to the court. All actions are illegal, are fixed. History query stored in the database of the U.S. Department of Homeland Security. To unblock your device and close your case you should pay a $200 file to Treasury account. Pay to unblock device with iTunes Gift Card. Your case will be closed immediately after the transaction processing! Avoid becoming a fraud’s victim! Evade the scams, that ask you to afford you iTunes Gift Card. Please, observe following rules for your safety: You mustn’t give your prepaid card number or your bank account details, till you are absolutely sure, that the person is conscientious. Remember, if somebody asks you to buy a iTunes Gift Card, it is a scam. Don;t show or report your iTunes Gift Card Code to anyone. Use only approved Apple partners.
Update 25 April 2016 - A new ransomware was discovered targeting Android users' files in Russia. This ransomware is being distributed using fake Android applications named "Домашний Порно Изврат," "RootChecker" and "Porn Video HUB+."
Here are some screenshots of Android ransomware targeted at users from Russia:
Fake applications ("Домашний Порно Изврат", "RootChecker" and "Porn Video HUB+") used in distribution of these ransomware infections:
Ransom demanding message presented in this scam (accusing Android users of viewing child pornography, etc.):
ВАШЕ УСТРОЙСТВО ЗАБЛОКИРОВАНО!За Просмотр запретного контента с элементами ПЕДОФИЛИИ, НАСИЛИЯ, ИНЦЕСТА, ЗООФИЛИИ и ГЕЙ-ПОРНО который строго запрещён Законом РФ загружены на сервер МВД,будет передано е прокуратору РФ в случае не оплаты штрафа,даже если вы разблокируете телефон самостоятельно! Причина блокировки обслуживания - посещение и просмотр запрещенных интернет ресурсов содержащие элементы порнографии с участием несовершеннолетних, элементы ПЕДОФИЛИИ, НАСИЛИЯ, ИНЦЕСТА, ЗООФИЛИИ и ГЕЙ-ПОРНО. Для предотвращения открытия уголовного дела и возобновления доступа к устройству,удалению всех Ваших данных с сервера, Вам необходимо оплатить штраф в размере 1000 Рублей в течении 15 часов. Следуйте инструкциям для оплаты:
1. Найдите терминал сотовой связи для оплаты VISA QIW1 WА1[Е7. 2. Введите номер телефона + 79688220910 З. В поле коментарий введите код -В1)95284680 4. Оплатите 1000 рублей 5. После поступления оплаты Ваше устройство будет автоматически разблокировано и все данные удалены с сервера в течении 3 часов. Если оплата не поступит в течении 15ч, ВСЕМ контактам Вашего телефона, а так же ВСЕМ Вашим контактам социальных сетей будет отправлено смс сообщение, о том что на вас заведено уголовное дело за просмотр ДЕТСКОЙ ПОРНОГРАФИИ. Попытки разблокировать телефон самостоятельно приведут к ПОЛНОЙ БЛОКИРОВКЕ Вашего телефона, а видео с Вашим участием будет ВЫЛОЖЕНО в социальные сети и УоиТиЬе с пометкой ПЕДОФИЛИЯ.А так же все данные с Вашего телефона будут переданны в ПРОКУРАТУРУ РФ для возбуждения уголовного дела.
Проверить оплату
How to Remove "Your device has been blocked" Ransomware from an Android Tablet or Phone?
Ransomware notifications (that are impossible to close) are loaded from third-party rogue applications. For example, BaDoink, VideoViewer, VideoPlayer, Network Driver System, Video Render, and PornDroid, among many others.
To eliminate the screen-blocking message, you must uninstall the rogue application which causes it.
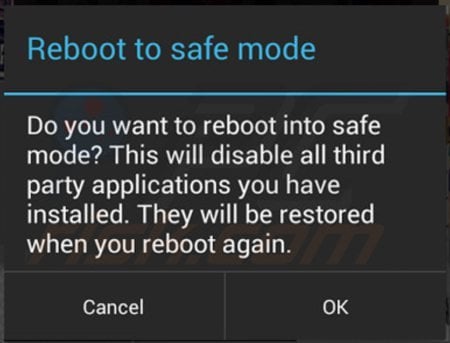
Boot your Android device into Safe Mode:
1. Hold down the power button on your device.
2. In the opened notification window, long-press the "Power off" option.
3. In the opened window, confirm that you wish to boot into Safe Mode by tapping "OK."
4. When your phone or tablet reboots, you should see a "Safe Mode" watermark (at the bottom of the screen). Go to your device Settings menu, tap "Apps" or "Application manager."
Touch the application you wish to uninstall (which causes the rogue ransom-demanding message to appear on your device, for example, PornDroid).
Some newer Android devices boot into Safe Mode by simultaneously holding the volume up and volume down button when restarting.
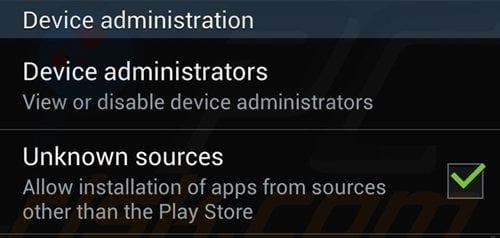
To protect your Android device from these ransomware infections, disallow third-party application installation. Go to "Settings," select "Security," scroll down, and uncheck the "Unkown sources" box.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.





▼ Show Discussion