Check If Your Mac is Not Infected With Crypto-Mining Malware

(updated)
Get Free Scanner and check if your computer is infected
Scan your Mac NowTo fix found issues, you have to purchase the full version of Combo Cleaner. Free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
What is Crypto-Mining Malware and How Check If Your Mac is Not Infected With?
The myth that Macs are in some ways invulnerable and come with built-in anti-malware 'force fields' is not true. Macs are affected by malware and have been for most of their existence. One of the first malware infections to become popularised, ElkCloner, affected Apple computers rather than the MS-DOS computers of the time.

With the surge in popularity of cryptocurrencies such as Bitcoin, Ethereum, and many others utilizing blockchain technology, a new type of malware has risen in conjunction with cryptocurrencies. These new malware strains are called 'crypto miners', and some have been infecting Macs.
What exactly is Crypto Miners?
Currently, there are two ways you can get cryptocurrencies. The first is to buy them and the second is to mine them. There have been instances of hacks targeting the wallets of cryptocurrency buyers. These often rely on hackers exploiting vulnerabilities within wallets on websites or servers.
Crypto miners rely on mining the actual currency. A crypto miner, sometimes referred to as a 'crypto jacker', can be defined as malware that uses the CPU power of the target device to mine cryptocurrency, with the profits returned to the attacker's wallet.
 Download Combo Cleaner to check if your Mac is infected with a Crypto Virus
Download Combo Cleaner to check if your Mac is infected with a Crypto Virus
The use and popularity of crypto miners and crypto jackers have become so widespread that researchers believe they are fast becoming more popular than ransomware by cybercriminals. Security researchers have stated that activity generated by Crypto Miners was the most detected network event in devices connected to home routers in 2017. This ascent of malware use is considerable.
In October 2017, the prevalence of Crypto Miner detections peaked at 116,361 events, with many of those detections occurring in Japan, India, Taiwan, the U.S., and Australia. To understand the appeal of Crypto Miners to cybercriminals, one needs to understand the financial motivation.
In February 2018, it was reported that one operation that installed malware on servers running Jenkins (automation software designed for web development) mined roughly 3.4 million worth of Monero. That is essential, a considerable sum by any standards.
Monero is a popular choice for criminals to mine because of its increased privacy and anonymity features. This situation is further made problematic by the availability of applications such as Coinhive, which allows owners of websites to mine currency when visitors visit their webpage. These applications are abused by cybercriminals to maliciously mine for maximum profit.
Crypto Miners present very real Dangers
Besides the ethical issues and issues of the illegality of crypto miners, these types of malware can provide real problems. Problems that can result in major financial loss for the victims, be they individuals or companies.
In February of this year, Metro reported that a two-floor apartment building in Artem, near Vladivostok, went up in flames. The fire was caused by a resident illegally using the apartment blocks' electricity to mine Bitcoin. It is believed that a power surge caused the circuits to overheat, fail, and result in a fire that gutted the apartment building.
Fortunately, in this instance, nobody lost their life. The above example did not involve a Crypto Miner, but it is not outside the realms of possibility one could cause such an event.
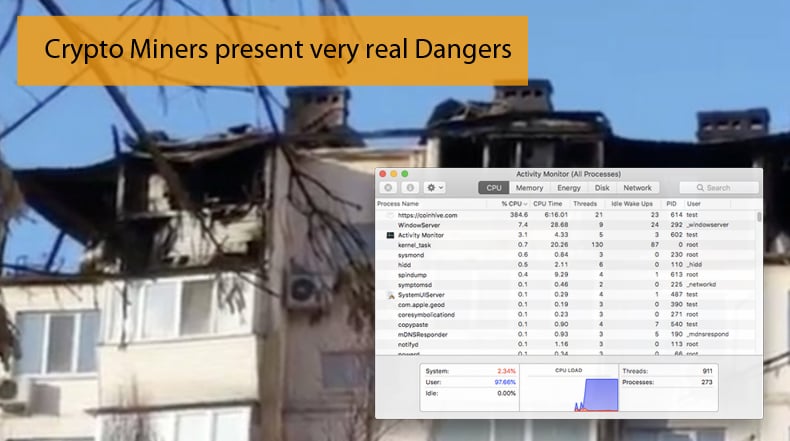
The miner uses devices' CPU resources (a smartphone, tablet, or personal computer), which causes an extra load upon the chipset. At the very least, this will increase the power consumption of the device. The device will also become noticeably slower.
While the CPU can handle increased loads for short periods, running at 100% for extended periods can cause a critical failure. In a recent article, security researchers at Radiflow, a company specializing in securing critical infrastructure, noticed miners infecting industrial control systems. The researchers feared such miners would inevitably have a severe impact on systems. In the same article, Marco Cardacci, a consultant for the firm RedTeam Security, which specializes in industrial control, said:
The major concern is that industrial control systems require high processor availability, and any impact to that can cause serious safety concerns. Such systems control things like power grids and dam wall, a catastrophic failure in those instances could be disastrous.
The above is a nightmare scenario, but Crypto Miners can easily cause significant failures on the devices we use daily. Russian security firm Kaspersky reported detecting mobile malware that mines Monero, bombards users with unwanted ads, and can even be used to launch denial of service attacks.
After two days of testing an infected device, it showed physical trauma: the overworked battery swelled up, damaging the phone's outer shell. Some cybercriminals want their miners to run for as long as possible and evade detection. They are thus programmed to operate when CPU cycles are not being utilized on other tasks.
Not all malware authors are as cunning. A hacker who simply copies code in the hope of striking it rich could drive a CPU incredibly hard for an extended period, thus placing the CPU at risk of catastrophic failure. This will result in the CPU or the entire device being replaced at an obvious expense to the victim.
How to detect if your Mac is infected
As mentioned above, Macs are not invulnerable to malware infections, or indeed, Crypto Miners. Security researchers recently reported on a miner being distributed via MacUpdate. The miner was called OSX.CreativeUpdate was designed to hide in the background and use the computer's CPU to mine Monero. The malware was spread by hacking the MacUpdate site, distributing maliciously modified copies of Firefox, OnyX, and other applications.
These now popular malware strains will inevitably evolve and change in the near future. They will have different key identifiers, and some will develop even more cunning ways to avoid detection. That does not mean that they cannot be detected. One of the key indicators that your Mac may be infected is CPU usage. This can be checked by simply opening a resource monitor on your computer to check if CPU usage is abnormally high. A resource monitor can be found on a Mac in the Activity Monitor that comes with the operating system.
The following could be indicators of infection:
If you see a spike in CPU usage when visiting a particular website, that should not otherwise be taxing the processor.
If you have all programs closed but CPU usage is still very high, you may have a crypto mining malware problem.
It is hard to say what "normal" CPU usage looks like since computer processing power and people's applications vary considerably. Nevertheless, a sudden, elevated level of CPU usage would indicate an abnormal increase in demand for processing power and possible infection.
Some miners are only active when you are visiting a website that features the miner in question. In these instances, the website or an advertisement may be infected and use your CPU to mine a cryptocurrency. To prevent this, you can take the following actions to prevent such abuse. You can also block JavaScript from running on a site known to be infected by simply using your browser's default privacy and content controls.
It is also advisable that you install an Ad-blocker. Ad-blocking software can also filter out known types of in-browser miners, such as Coin Hive (which is not necessarily malware). It can be embedded in websites without a visitor's knowledge, although its developers encourage website owners to disclose the script's presence to users.
 Download Combo Cleaner to check if your Mac is infected with a Crypto Virus
Download Combo Cleaner to check if your Mac is infected with a Crypto Virus
The above are examples of measures you can easily adapt to prevent such infections from occurring, or at least to allow you to detect them. Researchers at IBM have recently detected more sophisticated malicious miners. These are delivered through infected image files or by clicking on links leading to a malicious site. Such attacks tend to target enterprise networks with far more CPUs and resources on offer to the attacker.
As with their less sophisticated cousins, however, they can be detected by monitoring CPU usage. There are methods to help remove these more sophisticated strains if your system has been infected. There are excellent third-party applications designed to detect and remove Crypto Miners, such as Combo Cleaner.
Crypto Miners not the only Malware infecting Macs
While much of the above article addresses the understanding and detection of Crypto Miners, it is not only these strains of malware that can infect a Mac. While miners are predicted to be the dominant malware trend of this year, that nefarious title was held by ransomware for the previous year.
Ransomware can be defined as a malicious program that seeks to encrypt data so that users cannot access their files. Once files are encrypted, a ransom note is delivered, instructing how the payment must be made to decrypt the data. The data is effectively taken from victims until they pay a ransom. Payment is often required in Bitcoin or other cryptocurrencies of cyber criminals' choice.
A recent strain of ransomware seen to infect Macs was discovered in 2017. Called McRansom (not an original name), it was by no means the most sophisticated of ransomware. It could only encrypt a maximum of 128 files. The danger it posed was due to how poorly it was designed. Encrypting the files also 'mangled' them, so when the victim paid a 700 USD ransom, there was still no guarantee that the files could be accessed.
Another variant called KeRanger was discovered in 2016. It affected some 7,000 Mac users and was distributed via a compromised Transmission installer.
Adware is another type of very prevalent malware that can infect Macs. This is software designed to display advertisements, usually within a web browser. It can do this by either disguising itself as legitimate or piggybacks on another program to be installed.
Once the system is infected, the adware changes how the browser behaves by injecting ads into web pages, causing pop-up windows or tabs to open, and changing the homepage or search engine settings. This is done to funnel advertising dollars away from companies that pay for online ads and their own accounts. This is incredibly frustrating for the victims. To this extent, Mac users are advised to make sure browser pop-up blockers are activated to help prevent further infections.
Conclusion
It would be great if Macs were invulnerable to all types of malware infection. Unfortunately, they are not. Users must educate themselves on the threats they face - this greatly helps prevent your day from being spoiled by a cyber-criminal. Unfortunately, some are incredibly cunning, and you might not be able to detect that you have a problem until it is too late.
Programs such as Combo Cleaner are an extra measure of defense recommended for Mac users. The company specializes in the detection and removal of malware that targets Mac OS. They also have a dedicated team of researchers who continually detect future threats before they become your problem.
Share:

Karolina Peistariene
Author of how-to guides for Mac users
Responsible for collecting, analyzing, and presenting problem-solving solution articles related to macOS issues. Years of macOS experience combined with solid research and analyzing skills help Karolina provide readers with working and helpful solutions as well as introduce various features Mac has to offer.
▼ Show Discussion