Computer technician blog
Categories:
General - General posts, notices and other information.
Viruses - News and articles related to viruses, will be posted in this section.
Windows - How-To guides for Windows users.
Mac - How-To guides for Mac users.
You can subscribe to ![]() RSS Feed
RSS Feed
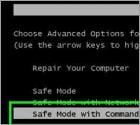
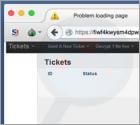
How to perform a System Restore using Command Prompt? (ransomware or virus is blocking Safe Mode)
The System Restore function restores operating system files to an earlier point in time. System Restore is useful when malicious software infiltrates a computer and damages the system files. Moreover, this function important when dealing with variants of ransomware infections that block computer screens. This tutorial describes the process of performing a System Restore using Command Prompt. In some cases, especially when dealing with ransomware infections, performing a System Restore is a complicated task, since modern fake antivirus programs and ransomware infections are capable of blocking an operating system's Safe Mode and Safe Mode with networking. This leaves one solution: performing a System Restore using Command Prompt.

"Your device has been blocked" - How to Remove Ransomware Infections From an Android Device?
Cybercriminals have been spreading ransomware viruses on Windows-based computers for some time. These infections became popular in mid-2006 and continue to infect personal computers and extort money from their victims.
Recently, security research began showing a rise in Android-based mobile ransomware infections. Usually, ransomware viruses exploit the names of authorities, including the FBI, USA Cyber Crime Investigations, and The ICE Cyber Crime Center - making fake claims that users must pay an amount of money (for supposed law violations such as watching pornography, using copyrighted files, etc.) to unblock their devices.
Google Chrome extension "Installed by enterprise policy" - how to remove?
This removal guide shows how to remove a Google Chrome extension that was "Installed by enterprise policy". Note that recently, there is a rise in adware infections, and in many cases, these potentially unwanted programs (PUPs) install on users' Internet browsers disguised as legitimate extensions. Commonly, potentially unwanted applications are bundled with free software downloaded from the Internet, the installation of which, is often a consequence of not paying close attention to the installation steps.
Internet Access Is Blocked by Malware. How to Fix It?
This tutorial describes how to re-establish Internet access if it’s blocked by malware. Some malware variants modify Internet browser settings by adding a Proxy Server. In such a case, you will be unable to visit any websites and unable to download the required software to eliminate the malware.
Other types of malware change the computer’s DNS settings or add various entries to your operating system’s Hosts file. Computer viruses can cause redirect issues or completely block the Internet connection by altering these settings. If you cannot access the Internet, and suspect that a virus infection causes this, check the settings below.
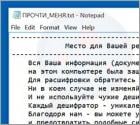
What is AMBA?
AMBA is ransomware-type virus that targets Russian websites. After infiltrating the server, AMBA encrypts most files on the system and adds the .AMBA or .RROD extension to the name of each encrypted file. A text file ("ПРОЧТИ_МЕНЯ.txt") is then created that contains a message (in Russian) encouraging server owners to contact cyber criminals via the email address provided.
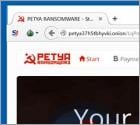
What is Petya?
Petya is ransomware distributed via malicious e-mails containing Dropbox download links to applications which, when executed, will install Petya on victims' computers. Research shows that these e-mails mainly target human resources (HR) departments of various German companies. After system infiltration, Petya encrypts portions of hard drives and makes ransom demands.

What is KimcilWare Ransomware?
KimcilWare ransomware targets websites using the Magento e-commerce platform (currently, it is not confirmed whether KimcilWare infects other platforms). During encryption, this ransomware adds a .kimcilware to each file stored on the server. Furthermore, it creates an index.html file containing a ransom-demanding message.
More Articles...
Page 87 of 90
<< Start < Prev 81 82 83 84 85 86 87 88 89 90 Next > End >>